Hacking is the advanced technology through which users can pierce through the security walls of any network or software to gain access to all the information inside. We all know that for hacking purposes, you must learn advanced and complicated languages and techniques that can cut through the cage of security. But is that enough to learn the languages and techniques and then apply them for the purpose of any operating system? No, it is wrong to say that you can do hacking without a good operating system, yet you will require a high-quality preferred OS for the various techniques. Talking the Mac, the best-ever operating system for computing devices, is good enough for hacking purposes. Again we would say that you cannot straightforwardly go with the Mac and start to hack. Some references must be made inside the Mac OS before it can be potentially utilized as a Hacking platform. Here in this article, we have written about all those things to be implemented on the Mac to make it ready for Hacking. Read the whole article and then apply all those things to your Mac! Also Read: How to Encrypt Your iOS and MAC Backups
Get Your MAC Ready for Hacking
Below we have mentioned the things or say tools that you will need before you start hacking on your Mac PC. So have a look at the complete guide below. Also Read: Top Best Hacking Tools For Windows, Linux, and Mac OS X
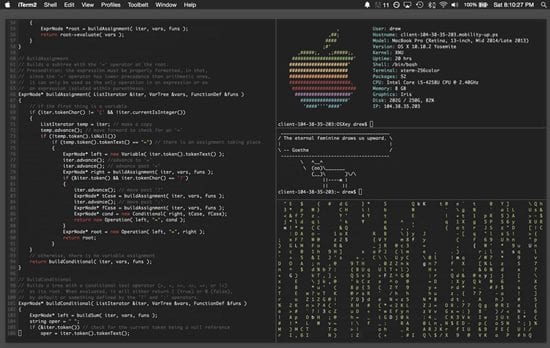
1. The better Terminal Installation
iTerm2 is the terminal app that you can install on the Mac device and hence get better advantages rather than the pre-installed terminal of the Mac. As we know, most of the hacking tasks are carried through commands generally processed inside the terminal only. The better terminal with more control features could be a great run for amazing achievements. To start up your device and make it a complete hacking module, you need this iTerm2 terminal.
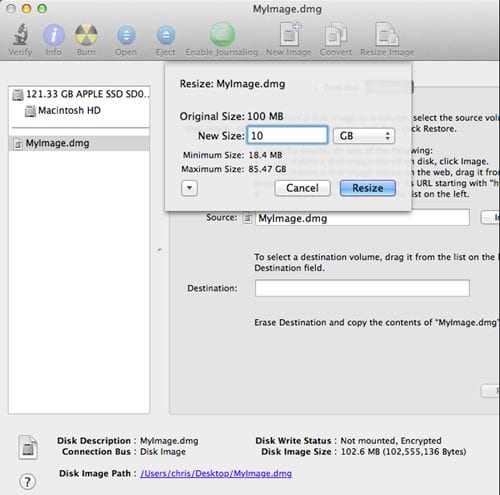
2. Encrypted Disk Images
The images of the data files and the packages stored inside the Mac need to be encrypted so that the other networks cannot interfere with it and harm it. It is also necessary to encrypt the disk images so that the data cannot be leaked and accessed by the other networks revealing your existence. Using various available tools, you can be able to encrypt the data of your device.
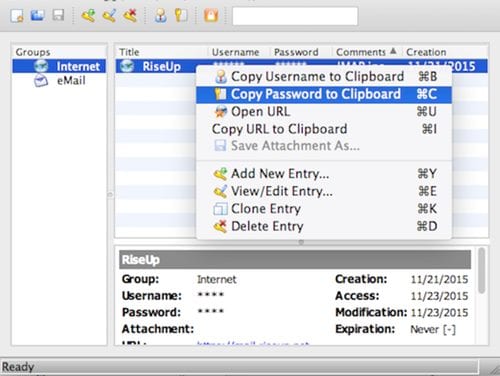
3. KeepassX
You will need to store passwords, and this is the best tool for that. KeePassX saves much different information, e.g., user names, passwords, URLs, attachments, and comments, in one single database. For better management, user-defined titles and icons can be specified for every entry.
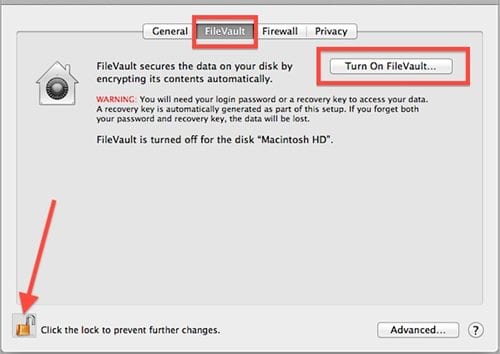
4. Disk Encryption
Full disk encryption again is wholly required to get your disk on the Mac encrypted so that no one can indulge inside it and hence harm it. The networks will be directly connecting with your disk, so making it secure means that you are preventing the networks from causing your device. Certainly, it is not difficult to encrypt the disk as you can do that through the software and tools available on the internet. You will have to be careful about that because encrypting the whole disk means you are actually locking the storage, and losing the encryption password can take away all your data access.
5. Install Kali Linux
The best coding platform for professionals and advanced users. It has been used by millions of hackers, technicians, and pro-tech users worldwide. Based on Linux this is the best-ever platform or the base for everyone willing to start to hack even the strongest networks inside the Mac only. Also Read: How to Record Your MAC’s Webcam Video So at the end of this article, you know how the Mac device can be turned into a better platform for hacking purposes, and you know all the things that help to transform the device for the purpose. The things you need to carry are quite easy, and about any average user can also carry out these implementations over their OS. We believe that you people would not find any difficulty regarding the information provided in the above post. If you find any issues, please tell us about them through the comments section below. Moreover, do try to like our article and share it more!