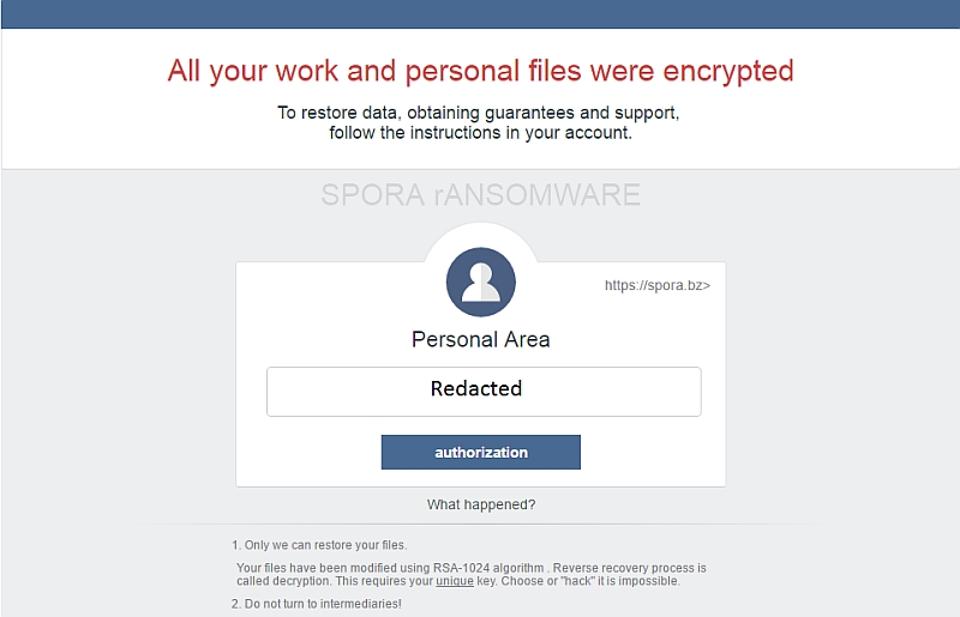
The first infections of Spora were known in the forums of Bleeping Computer and Kaspersky during the first week of the year. According to reports, the malware was spreading via email hidden in messages posing as invoices. The emails went with an attached ZIP file containing a file format HTA, which is an HTML.Además application, employing a double extension to appear normal, as PDF.HTA or DOC.HTA because on Windows computers it Hides the file extension, the user only sees the first dummy extension. Infection occurs when running this file, which will start the encryption process for computer files. While encrypting content, Spora extracts and runs a corrupted Word document that displays an error message, in order to distract the victim.
Unlike other families of ransomware, Spora not need Internet access and do not generate any network traffic, a feature that makes it very dangerous. This is because, by not connect to a server command and control, generates a different public key for each victim RSA, which does not work as the same decryption tool for all those infected. This ransomware does not encrypt the content, but only a selection of documents may be more important, including Excel files, Word, images, archives or backups. Once the process is finished, it shows the user a screen with the instructions to unlock the PC. However, it had only been detected in Russia, but now it has expanded to other countries as well, including Austria, the Netherlands, Japan, Saudi Arabia and much more. So, now it is clear that this dangerous ransomware can easily reach other territories as well, so simply stay aware and keep watch in your inbox of your email.